How to Solve a Puzzle Cube Blindfolded
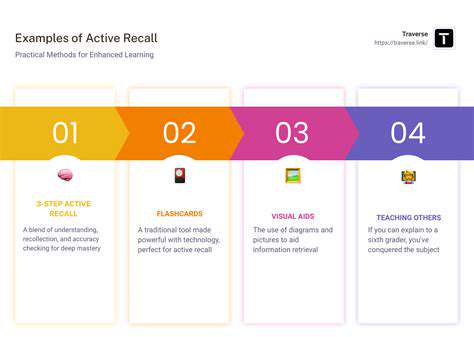
Understanding Memory Fundamentals
Building an effective memory system begins with grasping how human memory works. Our brains process information through three key stages: recording, retaining, and recalling details. These natural mechanisms inspire the design of artificial memory systems that can efficiently handle information.
Various memory types - including immediate sensory input, temporary working memory, and permanent storage - each serve unique functions. Designers must account for these differences when creating systems that mimic human memory capabilities. The duration and capacity limitations of each memory type directly impact system architecture decisions.
Designing for Efficiency and Capacity
An optimal memory system balances speed with storage potential. Quick access to stored data requires intelligent organization methods that minimize search time. The choice of data structures significantly impacts how rapidly users can retrieve needed information.
System architecture must allow for expansion as data volumes grow. Future-proof designs incorporate flexible scaling options without compromising current performance. This forward-thinking approach prevents costly redesigns when storage needs increase.
Implementing Robustness and Security
Reliable memory systems anticipate and handle potential failures gracefully. Built-in error detection and correction protocols maintain data accuracy during storage and retrieval operations. These safeguards protect against information degradation over time.
Data protection measures form the foundation of trustworthy systems. Advanced encryption and strict access controls prevent unauthorized viewing or alteration of sensitive information. Multi-factor authentication adds another layer of security for critical data stores.
Maintaining System Integrity and Performance
Consistent upkeep ensures long-term system reliability. Routine procedures like comprehensive backups and system health checks prevent data loss and performance degradation. Monitoring tools track key metrics to identify potential issues before they cause disruptions.
Automated error management systems continuously verify data integrity while the system operates. Regular software updates and hardware maintenance keep the memory system functioning at peak efficiency. These proactive measures extend the system's useful lifespan while maintaining security standards.
Executing Algorithms with Precision: The Art of Blind Solving
Understanding the Core Concepts
Effective algorithm implementation begins with thorough comprehension of basic principles and methods. Successful execution requires clear understanding of required inputs, desired outputs, and the transformation process between them. Modern frameworks simplify this process by handling technical complexities, letting users focus on logical implementation.
Input Validation and Data Preparation
Quality algorithm results depend on proper input handling. Robust validation ensures data meets specified format requirements before processing begins. Thorough data cleaning and normalization significantly improve algorithm accuracy and reliability. These preparatory steps often determine the success of subsequent operations.
Algorithm Selection and Configuration
Choosing appropriate algorithms from comprehensive libraries requires understanding their specific applications. Intuitive interfaces help users configure selected algorithms without deep technical knowledge. The selection process weighs each algorithm's advantages against the problem's unique characteristics.
Optimal algorithm choice balances processing efficiency with result quality. Different approaches suit different data types and problem complexities.
Execution and Monitoring
Real-time progress tracking enables immediate issue detection during processing. Detailed performance metrics help optimize resource allocation and identify potential bottlenecks. Comprehensive logging creates valuable records for future analysis and system improvements.
Results Analysis and Interpretation
Effective tools transform raw algorithm outputs into actionable insights. Visualization capabilities highlight important patterns in processed data. Accurate interpretation converts technical results into practical business decisions. Custom reporting features tailor output presentation to specific audience needs.
Integration and Deployment
Modern platforms simplify incorporation into existing business processes. Seamless connectivity allows algorithm results to feed directly into operational systems. Reusable components enable efficient scaling across multiple applications. Consistent performance across different environments ensures reliable deployment anywhere.
Read more about How to Solve a Puzzle Cube Blindfolded
Hot Recommendations
-
*Best Sci Fi Books to Read in 2025
-
*How to Start a Reading Journal
-
*Guide to Collecting Vinyl Records by Genre
-
*Guide to Self Publishing Your Book
-
*Guide to Reading More Books
-
*How to Solve a Megaminx Fast
-
*Guide to Identifying Edible Plants While Hiking (Use Caution!)
-
*How to Solve a 5x5 Rubik's Cube
-
*Guide to Building Advanced Lego Structures
-
*How to Capture Star Trails Photography